As factories continue to grow using project-to-project initiatives up to wholescale smart factory implementations, connectivity becomes more critical to enabling the technology and tools that accelerate change. A new generation of manufacturing applications require a new type of high-performance networking solution. Some of the applications include sensors for machine and process monitoring; video analytics for quality control; robotics and autonomous machines for operational efficiency; and redesigned production facilities that can be easily reconfigured to accommodate multiple product lines or modifications to production processes.
For this new generation of applications, manufacturers should consider Private Cellular Networks (PCNs). PCNs are highly secure, flexible, and very reliable with the ability to define Quality of Service (QoS) based on application-specific requirements. PCNs give CIOs a more secure, flexible, and cost-effective networking alternative than other currently available options. Securing PCNs requires a shift from securing Information Technology (IT) assets, such as servers, storage, and applications, that have characteristics of short lifecycles, to securing Operational Technology (OT) assets, such as IoT devices, sensors, manufacturing assets, where the lifecycle is typically 10-25 years.
Security is of paramount importance in the implementation of a PCN for all manufacturers – from aerospace defense contractors to semiconductor fabricators to automobile companies. As the number of connected devices and applications inside the manufacturing facility increases, so does the potential security threat.
Factors for a Secure PCN
Here are some factors to consider when implementing PCNs:
- Zero-trust architecture for OT environments: The zero-trust security model is based on a set of system design principles, which acknowledges that threats exist both inside and outside of traditional network boundaries. This model ensures that the concept of least privilege is applied for every access decision.
- Threat modelling: Threat modelling that is normally integrated into the organization’s security practices can be used to assess the introduction of the PCN. Examples include the STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege) and PASTA (Process of Attack Simulation and Threat Analysis) threat models.
- Vulnerability management: PCN assets must be integrated into an organization’s vulnerability and incident management programs.
- Supply chain: Great emphasis needs to be placed on having trusted suppliers, securing the use of open-source software, hosted infrastructure platforms, and ensuring secure software development.
Identifying Potential Threats
The first step in securing a PCN is to identify potential attack threats. The main components of a PCN are described below and shown in Figure 1:
- Mobile Core: The Evolved Packet Core (EPC) in LTE or the 5G Core (5GC) in 5G provides the intelligence and management of the cellular network. The network functions can be on premise, cloud-hosted or hybrid with the control plane in the cloud and the user plane on premise.
- Radio Access Network (RAN): In a PCN, the radios are known as Citizens Band Services Devices (CBSDs). The CBSDs are managed by a Radio Management System (RMS) that is typically cloud-hosted. The RAN layer connects the User Equipment to the Mobile Core and OT platforms.
- User Equipment (UE): UEs are the end-user devices in the network that need connectivity to the OT platforms. They can include mobile phones; tablets; machine connectivity for robots and autonomous vehicles; unmanaged devices such as sensors; and other IoT devices. Each UE must have a Subscriber Identity Module (SIM) or software-based electronic SIM (eSIM) to attach to the PCN.
- Network Management System (NMS): The NMS provides remote management and monitoring. Located on premise or in the cloud, it is integrated to a ticketing system supporting Day 2 Services.
- Spectrum Access Services (SAS): The SAS is a third-party application that manages the wireless spectrum used in the PCN.
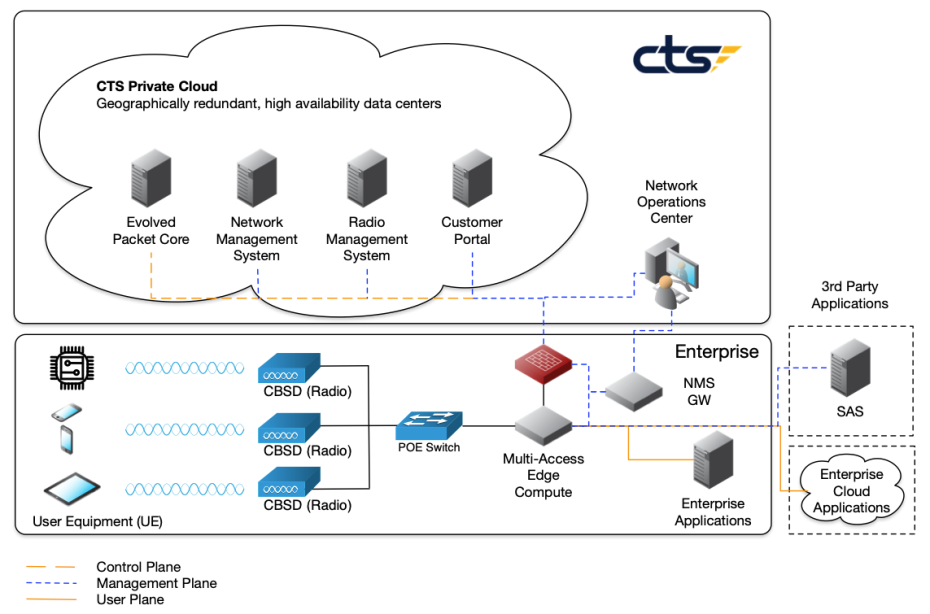 Figure 1: CTS PCN Architecture
Figure 1: CTS PCN Architecture
Potential attacks to a PCN can impact every network component:
- Mobile Core Networks: Bad actors will attack the control plane signaling network, destabilize the mobile core with authentication requests (Authentication Flooding), or exploit software vulnerabilities either in the application or the operating system.
- RAN: Bad actors can masquerade as a trusted RAN, tricking the UEs to connect to the untrusted device rather than to the real RAN. Bad actors can intercept data/voice traffic at the RAN level and route valid traffic to networks/systems they control, thereby facilitating further attacks.
- Transport Network: Data traffic can be intercepted through the backhaul network. Bad actors will steer or mirror data traffic to collect useful information or destabilize the data network.
- UE: UE attacks are executed through SIM compromise, where a bad actor uses a valid SIM card in another device to gain access to the network. Malware can be deposited on the UE which will be used to take over the device. Bad actors can instigate a Distributed Denial of Service (DDoS) attack by using botnets throughout the network.
- Mobile Infrastructure Systems: Bad actors can change network and equipment configurations to allow unauthorized access to infrastructure platforms such as the mobile core, RMS, or NMS.
- Third-Party Applications: Bad actors can infiltrate third-party applications and use the external IP network as an entry point into the PCN.
Applying Zero-Trust Principles to PCNs
PCNs benefit from 3GPP security practices, generally considered the most stringent, including zero-trust principles such as strong authentication and least privilege. These principles should be embedded by design.
Guarding Against UE Threats: Traditional IT techniques, including subscriber authentication and device access control, should be extended to the PCN to guard against unauthorized access to the device. Device to network connectivity is protected through adoption of SIM technology within the device, either a physical hardware SIM or an eSIM. Further device-level protection can be added through practices such as SIM locking and multifactor authentication.
Minimizing Device and RAN Attacks: The risk of UE or RAN attacks is minimized by the implementation of both network to device authentication and air interface encryption mechanisms. The Authentication and Key Agreement (AKA) protocol is used for authentication between the UE and the mobile core in a PCN. In addition, the LTE/5G air interface in a PCN is protected by 3GPP standards that have defined multiple encryption algorithms to safeguard data transmission.
Protecting Infrastructure Systems: On-premise mobile core, RMS, and NMS platforms should be secured through an extension of existing enterprise IT security practices, enabling management using existing network management tools.
Securing Backhaul Connections: Hardware security appliances can be used to protect the traffic over the S1 interface (backhaul) using Internet Protocol Security (IPsec) tunnels between the radios and the mobile core. Having IPsec on the backhaul helps maintain a zero-trust security in which nothing is trusted, and everything must be verified.
Summary
A company’s approach to securing their PCN should be no less rigorous than that of securing new IT architectures. There may be additional factors that require consideration when implementing the PCN, comprised of 3GPP architecture (UE, RAN, mobile core), non-3GPP defined architecture (switches, routers etc.), and OT (IoT devices). Some key practices are threat modelling, penetration testing, vulnerability assessments, border protection, and updating of security controls into the organization.
CTS provides custom, carrier-grade in-building and campus connectivity solutions for enterprises and mobile network operators, solving and managing the most complex networking challenges. CTS only provides one solution: the one that’s right for your business.
Opinions expressed by contributing authors are their own.